Security has own Model too
Another three weeks had passed. New topics, new activities and other stuff to do. Having a role model to society is a big factor to say that this country still needs you. And like me as a student, I have roles too. For the three weeks in our Information Security class, I am able to get familiarize with all the models presented in the class by Sir Justin Pineda. Organizing Security models is one topic we all been aware of. Sir Pineda was able to discussed three models. Bell-LaPadula model, Biba and Clark-Wilson model. Bell-LaPadula model is describing to the access of internet and having the controls which can be labeled on any objects. An access control to all objects having the permission or a clearance to the said objects before you can actually access it. The model have a so-called Security labels which divided to its range. "Top Secret" is the priority. "Public" on the other hand is the least priority. Bell-LaPadula model is a kind of Security model where protection and security cannot be determined clearly.


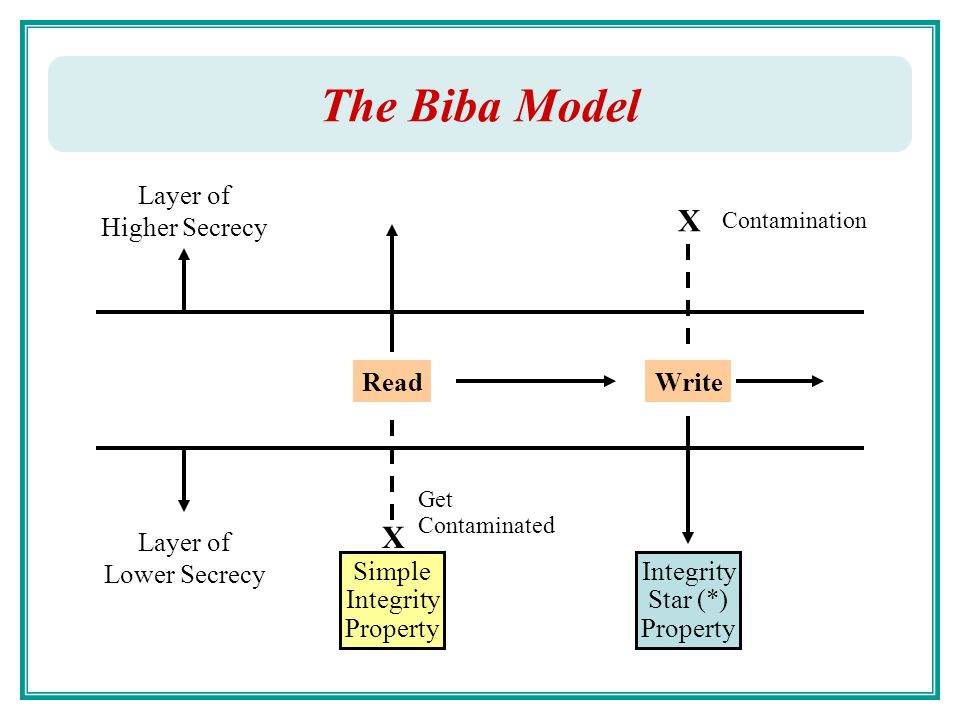
Meanwhile, Biba model or so-called Biba Integrity model is a kind of security model that illustrates as a rule for a protection of a data. The entities in the system are divided into subjects and objects. Biba model has a term used which is a "Secure state". It is a term to describe each state transition preserves the security by moving it to secure state.

On the last part, Clark-Wilson model was also discussed by our professor. This is a third part of the organization security. Clark-Wilson model like Biba is also an Integrity Integrity model.This model is also maintained by preventing corruption of data items in a system due to either error or malicious access to the system. It show how the data items in the system should be kept valid from one state of the system to the next and specifies the capabilities of a system. Clark-Wilson model has its goal to prevent unauthorized users from making modifications to one system.

All these models I have discussed is all about how security were arrange to its own perspective. It shows how to make things right especially when defining the level category like having one access based on your position. These three models prove that one employee should not be able to read all the confidentiality measures in a higher position of an another regular employee.

Comments
Post a Comment